-
Who we are
Introduction
We provide technology services that digitally transform our partners and generate business value. We offer a comprehensive range of services, including staffing and technology consulting, software engineering, and ongoing support. Our multidisciplinary expertise enables us to deliver innovative solutions that help our partners achieve their goals.

-
What we do
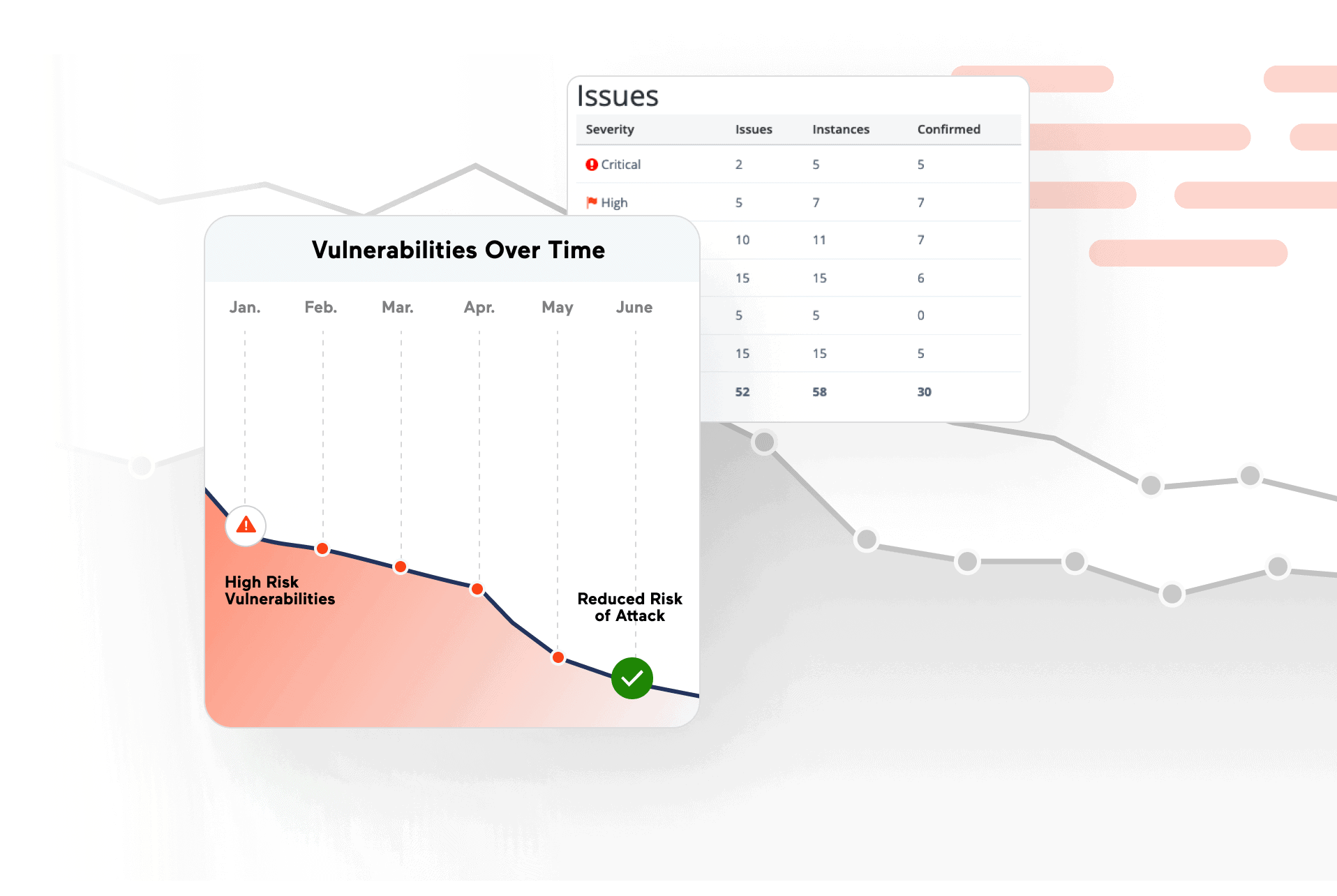
Security services
We’re dedicated to more than just immediate software solutions. Our expertise lies in creating a practical cybersecurity roadmap that aligns with global standards. By simplifying cybersecurity into three key factors—human, policy, and technology—we guide you through today’s complex landscape. Whether it’s empowering your employees with security awareness training or recommending cost-effective technical solutions, we’re here for your future security needs.

-
Contact